Jetpack 7.6 was released this week with several improvements to the plugin’s AMP compatibility. Automattic was one of the earliest publishing partners on Google’s AMP project, as well as the original author of the official AMP plugin for WordPress. This release makes three more Jetpack features compatible with AMP:
- Related Posts now display on AMP views.
- AMP images are now rendered via Jetpack’s image CDN if the module is active.
- AMP plugin is now capable of styling the Jetpack sharing buttons, without loading any additional CSS.
More AMP compatibility improvements are planned for the 7.7 milestone, including AMP support for the WordAds block.
Version 7.6 also fixes a security vulnerability in the Simple Payments description output. This fix only affects those who have Premium or Professional plans and are using the Simple Payments button to sell products or collect donations.
Jetpack is Beta Testing a Preview and Upgrade Nudge for Blocks Only Available on Paid Plans
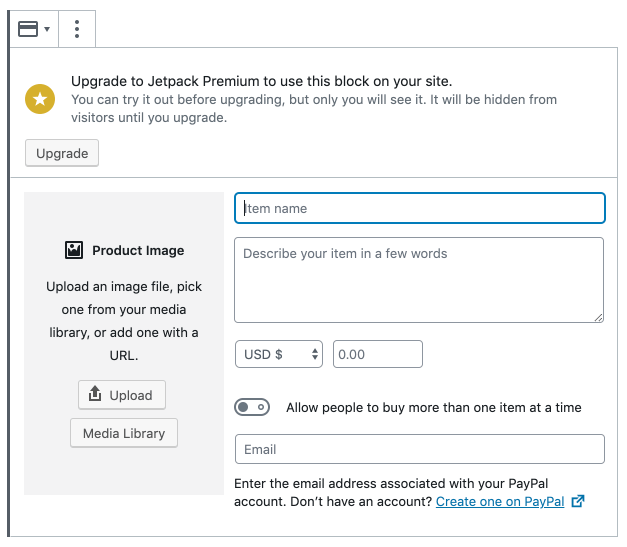
Jetpack is testing a new way of marketing its Paid plans inside the block editor. One of the more interesting additions to this release is that the plugin now allows for the insertion and preview of any Jetpack block in the editor, even if the block is only available via a Paid plan. Although it was included as part of the 7.6 release, it look like it’s currently only active for sites that have enabled beta testing.
The first iteration was merged as a generic solution that can be extended for all premium blocks but it currently only applies to the Simple Payments block. Prior to this update, users on the free and personal plans would not see the Simple Payments block in the block inserter. This change adds the Simple Payments block to the list of available blocks and allows users to insert and preview it. The block will not show up on the frontend unless the user upgrades.
Clicking on the upgrade nudge takes the user to the checkout with the plan pre-selected and then drops them back to the editor after they purchase the required plan for using the block. After the initial implementation with the Simple Payments block, the Jetpack team plans to do the same for the Recurring Payments, VideoPress, and WordAds blocks.
It’s easy to see why this controversial addition to the plugin was omitted from the release post. It adds new blocks for features that users cannot access without upgrading. The WordPress.org theme directory has struggled with a similar issue, which Justin Tadlock characterized as “crippleware,” where certain features are locked away behind upsells.
If Jetpack’s implementation catches on and other plugins follow suit, it could cause the block inserter to become a frustrating minefield. Users select from existing blocks, not knowing if the blocks they are inserting require a paid upgrade until the upsell pops into the editor. This is one block editor marketing tactic worth keeping an eye on as Jetpack rolls it out for more of its blocks that are restricted to Paid plans.