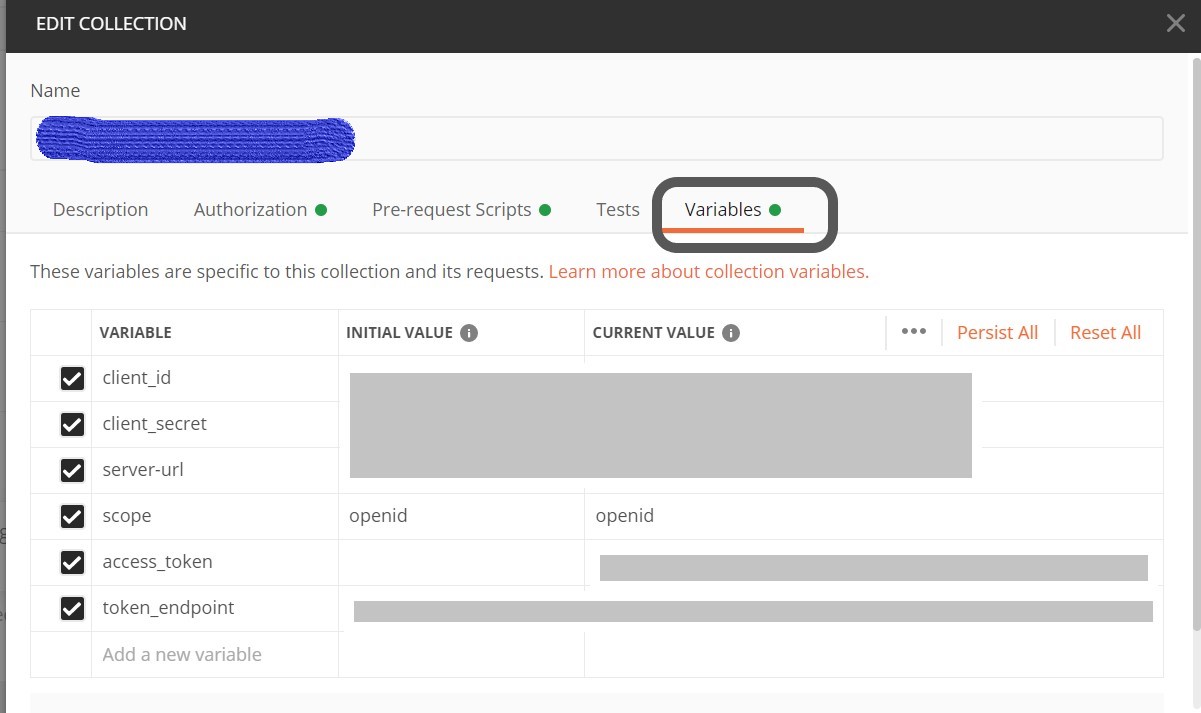
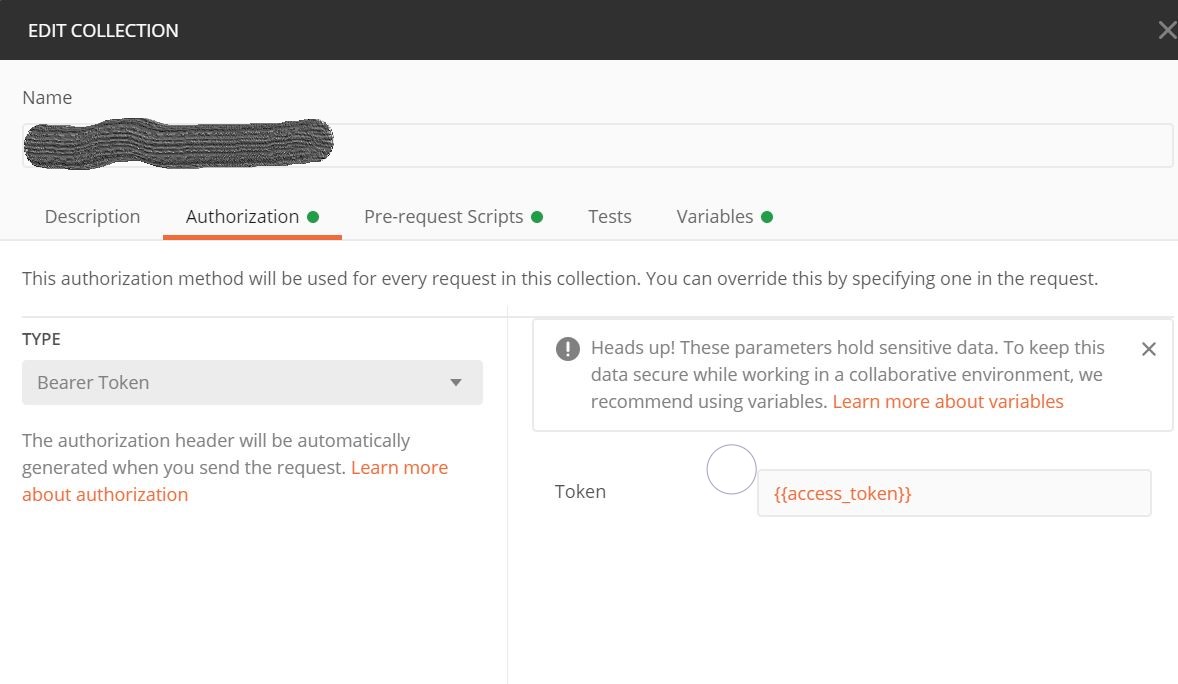
This week, we have news of a vulnerability in Argo CD that allowed leaking application secrets, a survey of the state of API security across three regions, a quick read on how to use Postman and OWASP Zap for API security testing, and finally, views on how to distribute authorization services in a microservice architecture.
Vulnerability: Argo CD Path-Traversal Vulnerability Enables Leaking Data
This week’s major news has been the vulnerability discovered in Argo CD, a popular continuous delivery platform.