Planning a microservices-based application — where to start? This architecture is composed of many aspects; how to break down this decoupled architecture? I hope that after reading this article, the picture will be clearer.
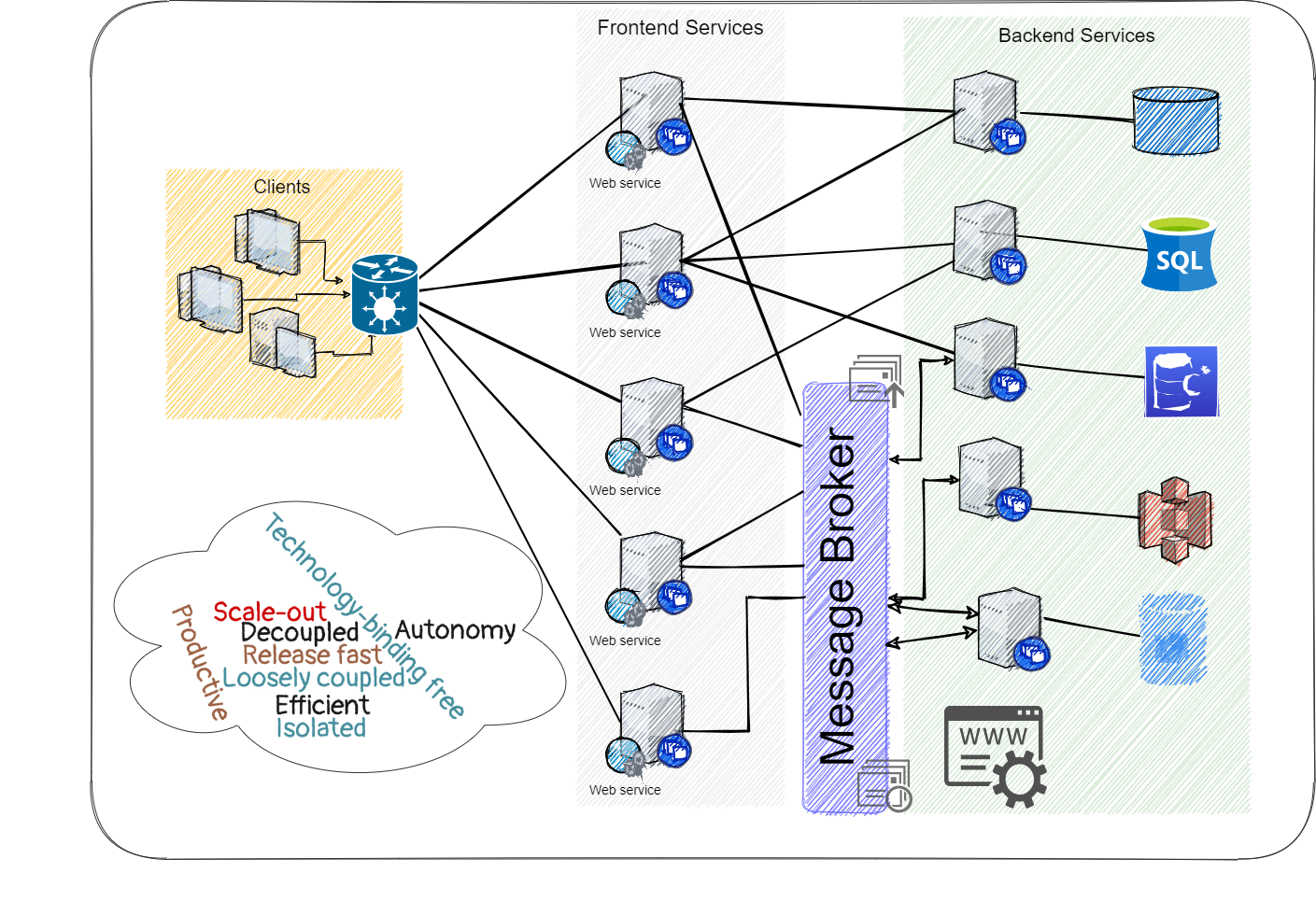
The Gist
- Why?
- The reasoning for choosing microservices.
- What to consider?
- The planning considerations before moving to microservices (versioning, service discovery and registry, transactions, and resourcing)
- How?
- Implementation practices (resilience, communication patterns)
- Who?
- Understanding the data flow (logging, monitoring, and alerting)
Building a viable microservices solution is attributed to the technical platform and supporting tools. This article focuses on the technical foundations and principles without diving into the underlying tools and products that carry out the solution itself (Docker, Kubernetes or other containers orchestration tool, API Gateway, authentication, etc.).

