We get thousands of global visitors every day on WPBeginner, so we know how important content delivery networks are for website performance.
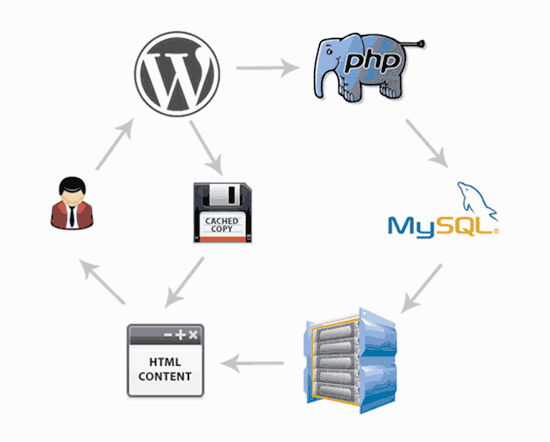
A CDN is a service that can significantly speed up your website. It works by caching and serving your website content from the servers nearest to your user’s location, reducing your page load time.
While we use Cloudflare on our own site, we know there are lots of other great options for WordPress users. That’s why we have tested the top options on the market, paying attention to the location and number of data centers, pricing, and user-friendliness.
In this article, we will show you the best WordPress CDN providers to speed up your website.

Expert Tip: Are you looking for more ways to speed up your WordPress website? It might be time to call in the experts.
Our experts will do a full performance audit on your website and then optimize it for lightning-fast loading times. Check out our WPBeginner Site Speed Optimization Service today!
How Does a CDN Help WordPress Sites?
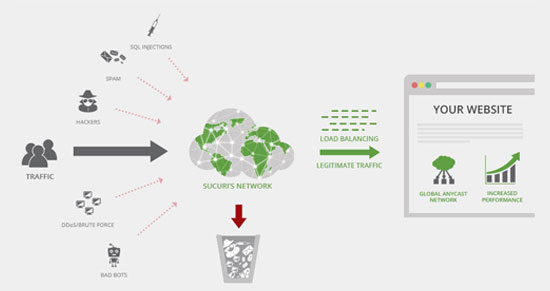
A CDN is a global network of servers that saves your website’s static content, such as HTML, CSS, and JavaScript files, in a cache. When a user visits your site, the CDN will serve the content from the server closest to the user, making it load faster.
With a CDN, your website will be much faster and less likely to crash when the traffic is high. This is because your site will rely on multiple CDN servers (called edge servers) instead of just a single origin server to deliver your content.
Here are some benefits of using a CDN:
- You get a faster page load speed. CDNs can decrease latency, or the time it takes for a server to deliver content to a browser.
- Your site will also be more SEO-friendly. This is because Google prioritizes web pages with good user experience, such as how fast your pages load.
- You get better uptime. CDNs use load balancing, so when one of the edge servers fails, the others can cover for it and keep the site running.
- You can make your WordPress website more secure against distributed denial of service (DDoS) attacks. The CDN will absorb and route the attack’s traffic to the network of servers to avoid overwhelming the origin server.
- You can reduce your WordPress hosting’s bandwidth usage, meaning you won’t need to upgrade to a more expensive hosting plan.
For these reasons, many WordPress website owners use CDNs to make their sites faster and more secure. So, let’s take a look at some of the top WordPress CDN services and how they stack up against each other.
Why Trust WPBeginner?
At WPBeginner, we have 16+ years of experience in running WordPress websites, optimizing them for speed, and reaching readers all over the world. We have also thoroughly tested each of the CDN services mentioned in this article.
For more details, just see our editorial process.
1. Bunny.net

Out of all the CDN services we have reviewed, Bunny.net is the best WordPress CDN on the market. Their WordPress plugin is easy and fast to set up, so you can start using the CDN right away.
Our team has been using Bunny CDN on OptinMonster because their pricing is very affordable for small businesses. If you are based in North America, then the pricing is just $0.01 per GB.
Not sure how much the total will be? Bunny.net has a handy calculator you can use.

They also have data centers worldwide, so you can reach users anywhere they are based. Simply select one of its 123 PoP (point of presence) locations across North America, South America, Asia, Africa, the Middle East, and Oceania.
Bunny.net knows that beginner WordPress users may be new to CDN services. That’s why they provide 24/7 customer support through live chat to help their customers, and they typically respond within an average of 5 minutes.
Pros of Bunny.net:
- User-friendly control panel to manage your CDN features, like activating your free SSL certificate in one click or clearing your cache to keep your content updated.
- Wide network coverage with its 123 and growing PoP locations.
- Video CDN to load videos faster.
- Up to 80% image optimization to reduce the size of your image files.
- 99.99% global Service Level Agreement, which means if your website is down, you will be eligible for credits to offset any loss caused by the outage.
- Real-time analytics to help you pinpoint performance issues on your website.
Cons of Bunny.net:
- There is no free tier, though there is a 14-day free trial.
Why we recommend Bunny.net: This high-performance CDN service is one of the best options for beginner WordPress users. Despite their affordability, Bunny.net has everything you need to make your website faster and offer a better user experience.
2. Cloudflare

Cloudflare is known as the best free CDN for small business WordPress websites. With a global network of 310 cities and 120 countries, you can rest assured that your site will always be online.
Setting up Cloudflare CDN in WordPress is easy. All you need to do is sign up for a plan, add your website to Cloudflare, and replace your domain’s nameservers with Cloudflare’s.
Cloudflare’s free plan also includes unmetered DDoS protection. This means Cloudflare will detect and mitigate DDoS attacks without limiting the traffic volume that can be protected.
We actually use Cloudflare for their paid security and CDN services on WPBeginner, and we have been very happy with their fast performance, huge CDN network, and excellent uptime.
For more details, you can see why we switched from Sucuri to Cloudflare.
Pros of Cloudflare:
- Cloudflare’s global network coverage is vast.
- The CDN has a built-in web application firewall to protect users against not just DDoS attacks but also other threats, like email spammers.
- Simple bot mitigation to differentiate legitimate bots, like search engine crawlers, from malicious bots like DDoS attackers or phishing campaigns.
- Special tools to handle dynamic content caching and delivery to make your site faster.
Cons of Cloudflare:
- There is no uptime guarantee for Free and Pro plan users.
- Direct support is only available for paid plan users.
Why we recommend Cloudflare: We use a paid Cloudflare plan on WPBeginner for our security and CDN needs. Overall, we appreciate how fast the Cloudflare CDN is, along with its advanced firewall rules to keep our website safe.
3. Sucuri

Sucuri is one of the most popular website security companies out there. Besides offering powerful website security features, they provide an easy-to-use CDN that’s optimized for WordPress.
To use Sucuri’s CDN, you need to sign up for one of their website security platform plans, which includes a web application firewall (WAF).
You can then add your site to the WAF, activate the firewall by changing your site’s DNS settings, and choose a CDN caching option. Besides speeding up your site and preventing DDoS attacks, the WAF also blocks spam and malware.
Sucuri’s data centers are vast, with locations in North America, Europe, and Asia. They also have CDN edge servers operating on Amazon Web Services in Australia and Brazil.
Pros of Sucuri:
- According to Sucuri, they can improve website performance by 60%.
- Multiple caching options, so you can choose the one that suits your site’s needs best. These include minimal caching, which is great if your site has lots of dynamic content (e.g., personalized text).
- Automatic SSL certificate installation for your firewall server to protect your data as it is being transmitted.
- Automatic malware removal, meaning Sucuri will delete any malware that it detects right away.
- For small business owners, Sucuri offers a basic firewall with CDN plans that start at $9.99 per month.
Cons of Sucuri:
- You cannot use the CDN alone as you have to purchase it with Sucuri’s main security features.
Why we recommend Sucuri: Sucuri is a great option if you are looking for a combination of WordPress security features and a CDN. It’s also pretty affordable, making it an excellent choice for small businesses.
4. KeyCDN

KeyCDN is another good option for a WordPress CDN service. It has a user-friendly CDN Enabler plugin that can automatically rewrite your website URLs to serve them through the CDN.
With the CDN Enabler plugin, you get more control over how your CDN works. For example, you can select what type of files need to be served using the CDN to focus on only the essential elements of your website.

You can also instantly purge your CDN cache right from your admin area. As a result, you can keep your website content up-to-date.
KeyCDN’s network of servers is spread across the Americas, Africa, Europe, Asia Pacific, and Oceanic regions. This way, your site always performs fast no matter where your audience is.
Pros of KeyCDN:
- High-performance CDN with support for HTTP/2, GZIP compression, IPv6 support, and image processing, all of which are important features that contribute to faster load times.
- Instant CDN purge right from the CDN Enabler plugin to easily update your website content.
- Pay-as-you-go pricing with a low minimum charge of $4 per month.
- Free 14-day trial with no credit card required.
Cons of KeyCDN:
- Despite the low minimum charge, you must purchase a minimum of $49 worth of credit to use KeyCDN.
Why we recommend KeyCDN: This CDN service’s wide network coverage, easy-to-use plugin, and affordable pricing make it worth recommending for small business owners who are just starting out. Just remember to have at least $49 worth of credit in your account to use it.
5. RocketCDN

RocketCDN is a WordPress CDN service offered by the same team as WP Rocket, one of the most popular WordPress caching plugins. That plugin has powered over 3 million websites, so you know you are in good hands with RocketCDN.
RocketCDN is powered by Bunny.net, which means they also have a global network of over 120 edge locations. However, what makes them different is their respective pricing models.
Instead of a pay-as-you-go scheme, RocketCDN comes in a single plan costing $8.99 per month. This already includes unlimited bandwidth for all regions, so you won’t have to worry about hitting any data caps or slow speeds due to limited resources.
When you activate RocketCDN, they will automatically adjust the settings of your website to ensure that it runs smoothly and quickly. These settings include Gzip compression and serving assets over HTTP/2.
Pros of RocketCDN:
- Monthly pricing with unlimited bandwidth, which can be a good option if you don’t want the hassle of calculating your own resource usage.
- Easy WordPress setup, as you only need to install their plugin and activate their API key.
- Everything is enabled for you once the CDN is active, from Gzip compression, and HTTP/2 support, to serving all images using CDN.
- Automatic canonical header setup so that search engines know which version of your website to show even though some of your assets are served using a CDN address.
Cons of RocketCDN:
- Compared to other CDN solutions on the list, RocketCDN’s features may seem too basic.
- No free trial.
Why we chose RocketCDN: Many WPBeginner users use WP Rocket for their websites, and RocketCDN is one of the best solutions to complement this caching plugin.
6. Imperva

Imperva is a cyber security company that offers many website and application protection solutions, including a CDN. They have 62+ data centers with 10 TB per second capacity, which is very high.
If your site receives 1 million visitors per day, and each visitor downloads 1 MB of data, Imperva could handle all that traffic without breaking a sweat.
Additionally, Imperva has self-service customization. This means you can decide how content is cached or traffic is routed based on factors like device type and user location. This feature can help optimize your website’s performance and reduce costs.
Pros of Imperva:
- Large bandwidth capacity to handle high traffic volume, making it perfect for online businesses.
- Self-service customization feature to configure how the CDN behaves to optimize performance.
- 99.999% uptime guarantee with a 3-second mitigation SLA, which means downtime is extremely low, and Imperva promises to fix any issue within 3 seconds.
Cons of Imperva:
- The self-service customization feature may be too advanced for the average WordPress user.
- There is no fixed pricing, and you have to contact their team for custom pricing.
Why we chose Imperva: When reviewing Imperva, we were thoroughly impressed by their high-performance CDN and advanced features that not all CDNs provide. We recommend Imperva if you have a growing, multinational business.
7. Amazon CloudFront

Last but not least, we have Amazon CloudFront. It’s a powerful WordPress CDN service for people who use Amazon services like Amazon SES and Amazon Web Services (AWS).
That said, despite its name, this WordPress CDN solution works with many other hosting providers, not just AWS.
When you use CloudFront, you will also get the AWS Shield Standard automatically enabled. This technology is like a more comprehensive version of DDoS protection, securing your website against attacks at all network layers.
Amazon CloudFront has 600+ points of presence in 90 cities across 47 countries, so its CDN service has vast coverage. It also offers a free tier that allows you to send 1 TB of data from CloudFront each month at no extra cost.
Pros of Amazon CloudFront:
- Seamless integration with AWS services, so it’s a great option if you already use them.
- A global network of servers, with hundreds of points of presence worldwide.
- Robust security features at the edge servers to protect your content from DDoS attacks, malware, phishing, and other threats at all levels.
- Generous free tier plan, as 1 TB of data transfer can serve approximately 1 billion web pages.
Cons of Amazon CloudFront:
- Not the most beginner-friendly setup.
Why we chose Amazon CloudFront: If you run WordPress on AWS, then you already have a great WordPress CDN service at your disposal. The vast network and generous free-tier plan also make CloudFront worth recommending.
Bonus: Use a Hosting Provider With Free CDN
These days, many WordPress hosting providers come with their own custom CDN solutions. This way, you won’t have to pay extra to make your website fast and secure.
Hostinger, for instance, has a built-in CDN available for Business plan users or above. It includes features like WebP image compression, CSS and JavaScript minification, and a handy under-attack mode to fight rapid DDoS attacks.

SiteGround also has an excellent CDN feature designed specifically for users who receive traffic from multiple countries. The team behind it has reported that loading speeds have increased by 20% on average.
While a free plan is available, they also have a premium plan with unlimited monthly bandwidth.
On the other hand, some hosting providers like Bluehost and WP Engine have integrated third-party CDN services like Cloudflare.
Which Is the Best WordPress CDN Provider for Your Site?
After carefully evaluating all these top WordPress CDN services, we believe that Bunny.net is the best WordPress CDN on the market. It has a wide global network coverage and offers a great set of features at a reasonable price.
For people on a tight budget, Cloudflare’s free CDN plan can do the job. It comes integrated with popular web hosting providers like Bluehost and WP Engine. Plus, you get unmetered DDoS protection.
If you want a CDN focusing on security, then Sucuri is the one for you. Besides multiple caching options, you can get a powerful WAF with automatic malware removal and SSL installation.
WordPress CDN Services: Frequently Asked Questions
Now that we’ve covered the best WordPress CDN services, let’s cover some frequently asked questions about using a CDN.
Which CDN does WordPress use?
The WordPress software does not use any CDN as it is only a content management system that requires a hosting service to run. Instead, the user has the freedom to choose any CDN service they prefer.
How do I choose a CDN for my WordPress website?
To choose a CDN for your WordPress website, you can consider your website needs, your own budget, and the platform’s ease of use.
If you need a beginner-friendly CDN with affordable pricing, then look no further than Bunny.net. On the other hand, if your website handles a lot of sensitive data, then you may want a CDN with a good set of security features, like Sucuri.
Can I use Cloudflare CDN with WordPress, and how does it compare to other CDN services?
Yes, you can use Cloudflare CDN with WordPress. In fact, many hosting providers like Bluehost and WP Engine have Cloudflare integrated into their dashboards, so you can immediately use it.
While Cloudflare CDN is free, it has great unmetered DDoS protection. However, there is no direct support.
Does CDN increase website speed?
Yes, a CDN can increase your website speed and make it faster. It will cache your website content into multiple servers spread worldwide. When users visit your site, the server closest to them will deliver the content.
That said, many factors affect website speed, so we recommend implementing other best speed optimization practices as well. For more information, check out our ultimate guide to boost WordPress speed and performance.
Ultimate Guides to Boost Your WordPress Site Performance
- Fastest WordPress Hosting (With Performance Tests)
- Best WordPress Caching Plugins to Speed Up Your Website
- How to Speed Up Your WooCommerce Website
- How to Easily Optimize Images for the Web Without Losing Quality
- How to Reduce Time to First Byte (TTFB) in WordPress
We hope this article helped you find the best WordPress CDN solution for your website. You may also want to see our ultimate WordPress performance guide or our expert pick of the best website speed test tools.
If you liked this article, then please subscribe to our YouTube Channel for WordPress video tutorials. You can also find us on Twitter and Facebook.
The post 7 Best WordPress CDN Services in 2024 (Compared) first appeared on WPBeginner.