A geeky multi-tool capable of hacking into Wi-Fi networks and opening Tesla car charging ports has been making headlines recently. I've familiarized myself with Flipper Zero and performed basic penetration testing on my own network and system. In this post, I share the results.

What is Flipper Zero?
According to its makers, Flipper Zero is "a portable multi-tool for pentesters and geeks". It can capture infrared signals, emulate NFC chips, read RFID tags, execute scripts via BadUSB, and much more. Almost four years after its release, parts of the community are still uncertain whether Flipper is just a glorified universal remote control, a dangerous hacking tool that governments should seek to ban, or simply the Leatherman of penetration testing.
I wanted to find out for myself and bought a Flipper a few weeks ago. Now it's time to share my first experiences. This article seeks to clarify the capabilities and limitations of Flipper Zero, so that you can evaluate whether it's worth the couple of hundred bucks in your individual case. Additionally, I'll introduce you to basic penetration testing with the WiFi Devboard and Marauder firmware.
One important note: How much you can really do with Flipper Zero depends entirely on your skills. It's certainly a good companion for deepening your understanding of the electromagnetic spectrum and computer networking basics. Anything that could be described as "serious hacking purposes" will require a specific skillset, additional software and, depending on what exactly you're trying to achieve, other equipment.
Getting Started: Basic Things to Try Out with Flipper Zero
The official website provides comprehensive documentation on how to get started with your Flipper Zero. Hence, I'll focus on things that you can try out right away once you've inserted the Micro SD card, updated the firmware, and installed the qFlipper app on your desktop or mobile device.
Things to do with your Flipper Zero:
- Read and replicate the signals of all your remote controls
- Try to replicate your electronic car keys and replace them if it works (i.e., they're not protected)
- Check the RFID chips of your pets
- Backup your NFC tags (e.g., phones, cards, keycards)
- Use the universal remote on your devices
- Generate U2F tokens to manage secure access to your accounts
- Use the built-in GPIO pins for a multitude of hardware-related tasks and experiments
- Run a BadUSB demo on your PC or Mac and write your own scripts

Flipper Zeros interface reminds of an old Nokia phone
In terms of handling, the 10x4 cm (4x1.6 in) device is controlled by a simple, old-fashioned interface and an intuitive menu that will resonate with anyone who already was around during the Nokia era. However, if you don't like pressing real buttons, you can navigate the menu and control your Flipper with the app (requires Bluetooth).
While you're not using your Flipper, the device will display scenes from the life of a pixel-style dolphin, which you can level up by reading and emulating signals (does not impact functionality). This slightly tacky feature also turns the multi-tool into a Tamagotchi for geeks.
To interact with Wi-Fi networks, you'll need a devboard that can be connected via the GPIO pins. The next section of the article takes a closer look at how to use the Wi-Fi devboard with Flipper Zero.
Using the Wi-Fi Devboard for Penetration Testing and Rickrolling

With the Wi-Fi devboard and Marauder firmware, Flipper can sniff on networks and launch different attacks
To use the Wi-Fi module as described below, you'll first need to perform a firmware update and then flash the devboard with the Marauder firmware. Once you've installed the companion app on your Flipper, you're good to go.
You can access the controls in the Apps folder under "GPIO". Once there, you should first scan for Wi-Fi access points near you. This will provide you with a list of all networks around, including their names and corresponding MAC addresses.
NOTE: Only perform the following steps on your own networks for the purpose of penetration testing! Never attack networks that are not your own, as this would be illegal.
Once you have the list of Wi-Fi networks, you can select the network that you want to "attack". Marauder offers different attack modes. The simplest one is to deauthorize all devices connected to the Wi-Fi. If you execute this attack, you'll notice that all devices connected to your Wi-Fi network are automatically disconnected for a moment and have to reconnect.
Another attack mode is called "rickroll". If you execute it, a long list of fake access points is created displaying Rick Astley's song Never Gonna Give You Up line-by-line.
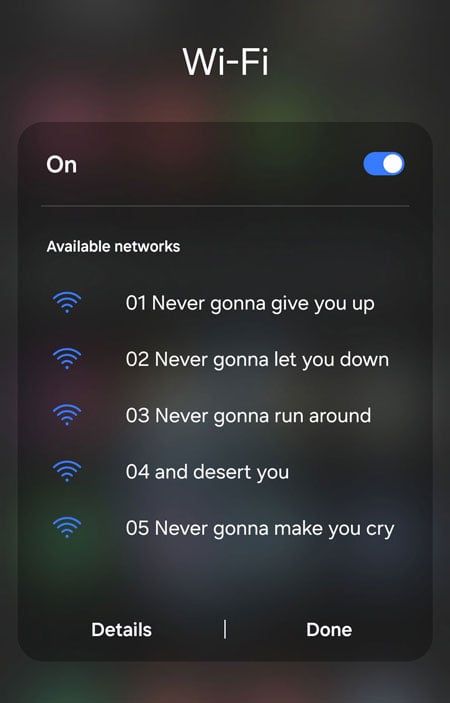
A rather harmless example of what you can do with the Marauder: Rickrolling networks with fake Wi-Fi access points
However, the Marauder firmware also enables more serious attacks that are great for penetration testing. The most basic method is sniffing authentication data. As explained in more detail in this video, you can sniff on a network while a device reconnects after being deauthorized, and then you can use simple freeware and a password list to decrypt the network credentials (i.e., the password). Of course, this method only works on unsafe passwords, and a simple way to protect yourself is to choose a secure Wi-Fi password (at least 12 characters with a combination of uppercase, lowercase, numbers, and symbols).
Combined, the Wi-Fi board and Marauder app can be used for various other purposes e.g., launching an "evil portal" that phishes login credentials, setting up a mobile wardrive, or reading GPS data. Would you like to hear more about any of those features? Let me know in the comments!
Conclusion: MacGyvering Still Requires Skills
While a Flipper Zero certainly won't give you magical hacking powers, it is a great (learning) tool for all those interested in secure communication and networking. It actually seems fair to think of it as the "Leatherman of pentesting". A Leatherman clearly isn't the best knife, the best screwdriver, or the best saw. But it includes the basic functionality of all those tools in a practical form. Similarly, Flipper Zero is a versatile multi-tool that allows you some serious MacGyvering if you possess the necessary skills. One last thing I want to point out is the surprisingly strong battery life. After dozens of hours of tinkering and many more in standby (with Bluetooth on), my Flipper's battery is still 98% charged on the first charge. However, besides the loading capacity the battery also seems to be an Achilles heel, as some users report issues with swollen power cells.
In this article, I've only scratched the surface of the many functionalities Flipper Zero offers. There's an ever-growing list of apps and add-ons, alongside an active community of people discovering new ways of using Flipper on a daily basis. For electronics geeks, the GPIO pins allow them to develop their own modules. Antennas can be used to greatly amplify the strength of infrared signals and the Wi-Fi board. There's much more to discover and I'm looking forward to the next experiment.