How to Setup RAID10 on Dell Servers
When it comes to IT Infrastructure, there are several components that play a vital role in a successful deployment, storage is one such component and it plays a crucial role in keeping the data safe and secure. Understanding different types of storage configurations is important and today we will discuss how we can achieve redundancy and performance by using RAID arrays. RAID stands for Redundant Array of Inexpensive/Independent Disks and RAID supports various types of configuration and in this article, we will focus on hardware RAID10 setup on DELL servers and if you are new to RAID and would like to learn more about it please go through this information.
Step 1
Boot the server and wait until you see the option to enter into RAID configuration <Ctrl + R> and once you enter into the configuration menu navigate through VD mgmt and PD mgmt screens and look for the available physical disks on the server. 
Chris’ Corner: More Like Scalable Vector Goodness
I’m going to do an SVG issue here, because I find that technology persistently interesting. It’s a bit of a superpower for front-end developers who know how it works and can leverage it when needed to pull of interesting effects. For example, this compelling line drawing scroll effect is powered by SVG features.
There have been some really cool SVG tools I’ve only just seen recently, and some great writing about SVG techniques. Warms my little heart to see SVG still being actively explored even as it sits rather dormant from a standards point of view.
Let’s start with some tools and resources, since those are easy to digest and if you really love one of them you’ll be all like thanks CodePen Spark, you’re a good newsletter and ya know that’s what we’re in it for.
Tech Icons

SVG icons tend to be single-color as a trend, but actual logos tend to involve brand colors and can often be multi-color. I like how it’s super easy to use, offering both downloads and quick copy-and-paste.
Durves
I can’t explain it but sometimes you need an SVG of a grid of dots that are waving. This allows you to control all the Aspects of that. Has some tearable cloth vibes.

svghub
Squiggles, scribbles, shapes and… other stuff.
I love this because they are the kind of things that are perfect for vector art, but that you don’t typically find in things like icon sets. One click to copy right to clipboard or download.

SVGMix
Big one! 193 Icon collections. I do like that they are grouped in collections, so in case you need a bunch of assets, there is a good chance they’ll go together aesthetically. I’m a big Noun Project guy, but find it isn’t quite as well organized into collections.

OK I suppose we’d better move on to some techniques and explanations.
SVG Gradients: Solving Curved Challenges

How do you get a color gradient to follow the path of SVG artwork? Michael Sydney Moore solved it by breaking up the art into smaller sections and applying gradients to each section.
This is an interesting contrast to another technique that Ksenia Kondrashova explains.
SVG viewBox
The viewBox on SVG is pretty simple really: it sets up the visible coordinate system where everything else is drawn. Interestingly, you can change it at any time, and it effectively acts as a camera, especially if you animate it.
Brad Woods has perhaps the best explanation of it I’ve ever seen, via an interactive post.

Making noisy SVGs
Turns out <feTurbulence> is up to the job of making a noise effect in SVG, but there is a little more to it to make it nice, as Daniel Immke writes up:
To create noise, I used the
<feTurbulence>filter which is explicitly for generating artificial textures but required quite a bit of fiddling to get to my liking. Then, I had to use other filter effects to eliminate color variance and blend naturally with the fill color selected, and finally apply the filter to the circle.

Noise sometimes feels like the perfect way to chill out the mathematical sharpness of vector art.
Also — did you know there is a weird trick to make noise with CSS gradients?
Responsive SVGs
There is a technique in this post from Nils Binder where he stretches just a part of an SVG according to variable content elsewhere and I love it.

Speaking of responsive… did you know the illustration in Ethan’s original article was responsive in itself?
Making SVG Loading Spinners: An Interactive Guide
This is part of what makes SVG so attractive to me: simple primitives that all combine together to do elegant things. Here, to make a specific kind of fun spinner, Sébastien Noël uses
<circle>with astrokestroke-dasharrayto control exactly how the stroke should be dashedstroke-linecapto control the nice look of the dashed partsstroke-dashoffetto control the position of the dashes@keyframeanimation to animate thestroke-dasharraymaking it feel like a spinner.

Icon transcendence: customizing icons to complement fonts
This one is from the “I hope your client has a lot of money” files. I love the idea but it’s wild. The idea is that SVG icons could swap out to match the vibe of the font they are next to.

But by “swap out”, really, somehow, it’s the same source icon.
Although these icons look quite differently visually, they were actually crafted by using the single source icon you saw above as a reference. For each of the fonts here, we’ve modified that source icon, thus producing a custom icon that better matches the style and mood of each font:
11 Things Every Website Footer Needs with Real Examples
A website footer is the section you can find at the bottom of a website, typically shown on all pages …
11 Things Every Website Footer Needs with Real Examples Read More »
The post 11 Things Every Website Footer Needs with Real Examples appeared first on .
How to Optimize Website Content for International Audiences

Shipping Tumblr and WordPress
Didya see that Tumblr is getting a WordPress makeover? And it’s not a trivial move:
This won’t be easy. Tumblr hosts over half a billion blogs. We’re talking about one of the largest technical migrations in internet history. Some people think it’s impossible. But we say, “challenge accepted.”
Half a billion blogs. Considering that WordPress already powers somewhere around 40% of all websites (which is much, much higher than 500m) this’ll certainly push that figure even further.
I’m sure there’s at least one suspicious nose out there catching whiffs of marketing smoke though I’m amicable to the possibility that this is a genuine move to enhance a beloved platform that’s largely seen as a past relic of the Flickr era. I loved Tumblr back then. It really embraced the whole idea that a blog can help facilitate better writing with a variety of post formats. (Post formats, fwiw, are something I always wished would be a WordPress first-class citizen but they never made it out of being an opt-in theme feature). Tumblr was the first time I was able to see blogging as more than a linear chain of content organized in reverse chronological order. Blog posts are more about what you write and how you write it than they are when they’re written.
Anyway, I know jobs are a scarce commodity in tech these days and Auttomatic is looking for folks to help with the migration.
I was about to say this “could” be a neat opportunity, but nay, it’s a super interesting and exciting opportunity, one where your work is touching two of the most influential blogging platforms on the planet. I remember interviewing Alex Hollender and Jon Robson after they shipped a design update to Wikipedia and thinking how much fun and learning would come out of a project like that. This has that same vibe to me. Buuuut, make no illusions about it: it’ll be tough.
Shipping Tumblr and WordPress originally published on CSS-Tricks, which is part of the DigitalOcean family. You should get the newsletter.
If I Was Starting My Career Today: Thoughts After 15 Years Spent In UX Design (Part 1)
My design career began in 2008. The first book that I read on the topic of design was Photoshop Tips And Tricks by Scott Kelby, which was a book about a very popular design tool, but not about user experience (UX) design itself. Back at the time, I didn’t know many of the approaches and techniques that even junior designers know today because they weren’t invented yet, and also because I was just beginning my learning journey and finding my way in UX design. But now I have diverse experience; I’m myself hiring designers for my team, and I know much more.
In my two-part series of articles, I’ll try to share with you what I wish I knew if I was starting my career today.
“If you want to go somewhere, it is best to find someone who has already been there.”
— Robert Kiyosaki
The two-part series contains four sections, each roughly covering one key stage in your beginner career:
- Master Your Design Tools
- Work on Your Portfolio
- Preparing for Your First Interviews: Getting a First Job
- In Your New Junior UX Job: On the Way to Grow
I’ll cover the first three topics in this first article and the fourth one in the second article. In addition, I will include very detailed Further Reading sections at the end of each part.
When you’re about to start learning, every day, you will receive new pieces of evidence of how many things you don’t know yet. You will see people who have been doing this for years and you will doubt whether you can do this, too. But there is a nuance I want to highlight: first, take a look at the following screenshot:
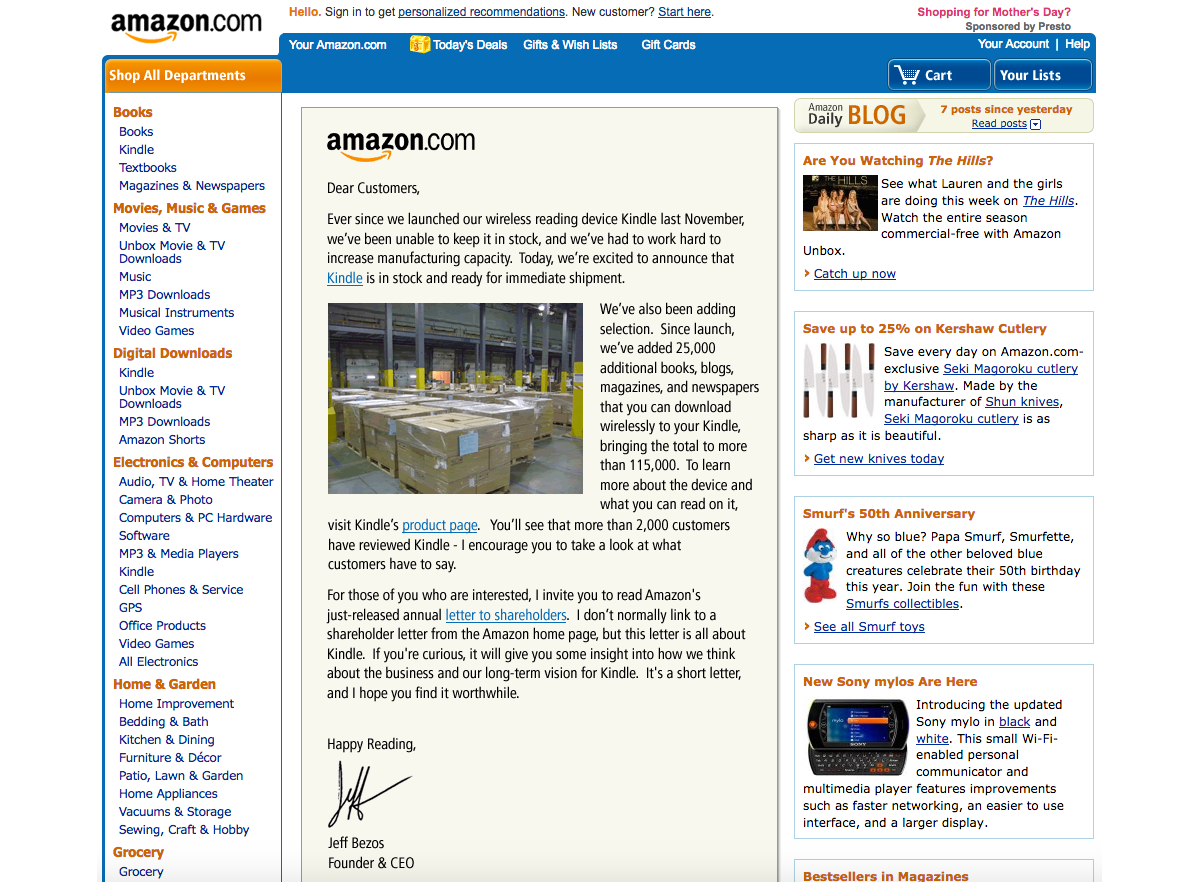
This is the Amazon website in 2008 when I was about to start my design career and received my first paycheck as a beginner designer.
And this is how Amazon looked like even earlier, in 2002:
 Source: versionmuseum.com. (Large preview)
Source: versionmuseum.com. (Large preview)
In 2002, Amazon made 3.93 billion US dollars in profits. I dare say they could have hired the very best designers at the time. So today, when you speak to a designer with twenty years of experience and think, “Oh, this designer must be on a very high level now, a true master of his craft,” remind yourself about the state of UX design that existed when the designer’s career was about to start, sometime in the early 2000s!
A lot of the knowledge that I have learned and that is over five years old is outdated now, and the learning complexity only increases every year.
It doesn’t matter how many years you have been in this profession; what matters are the challenges you met in the last few years and the lessons you’ve learned from them.
Are you a beginner or an aspiring user interface/user experience designer? Don’t be afraid to go through all the steps in your UX design journey. Patience and a good plan will let you become a good designer faster than you think.
“The best time to start was yesterday. The next best time is now.”
— H. Jackson Brown, Jr.
This was the more philosophical part of my writing, where I wanted to help you become better motivated. Now, let’s continue with the more practical things and advice!
Getting Started: Master Your Design ToolsWhen I was just beginning to learn, most of us did our design work in Adobe Photoshop.
In Photoshop, there were no components, styles, design libraries, auto layouts, and so on. Every screen was in another PSD file, and even making rounded corners on a rectangle object was a difficult task. Files were “heavy,” and sometimes I needed to wait thirty or more seconds to open a file and check what screen was inside while changing a button’s name or label in twenty separate PSD files (each containing only one design screen, remember?) could take up to an hour, depending on the power of your computer.
There were many digital design tools at the time, including Fireworks — which some professionals considered superior to Photoshop, and for quite a few reasons — but this is not the main point of my story. One way or another, Photoshop back then became very popular among designers and we all absolutely had to have it in our toolset, no matter what other tools we also needed and used.
Now computers are much faster, and our design tools have evolved quite a bit, too. For example, I can apply multiple changes to multiple design screens in just a few seconds by using Figma components and a proper structure of the design file, I can design/prototype responsive designs by using auto-layout, and more.
In one word, knowing your design tool can be a real “superpower” for junior UX designers — a power that beginners often ignore. When you know your tool inside-out, you’ll spend less time on the design routine and you’ll have more time for learning new things.
Master your tool(s) of choice (be it Figma Design or Illustrator, Sketch, Affinity Designer, Canva, Framer, and so on) in the most efficient way, and free up to a couple of extra hours every day for reading, doing tutorials, or taking longer breaks.
Learn all the key features and options, and discover and remember the most important hotkeys so you’ll be working without the need to constantly reach for your mouse and navigate the “web” of menus and sub-menus. It’s no secret that we, designers, mostly learn through doing practical tasks. So, imagine how much time it would save you within a few years of your career!
Also, it’s your chance: developers are rolling out new features for beginner designers and pro designers simultaneously, but junior designers usually have more time to learn those updates! So, be faster and get your advantage!
Getting Started: Work On Your PortfolioYou need to admit it: your portfolio (or, to put it more precisely, the lack of it) will be the main pain point at the start.
You may hear sometimes statements such as: “We understand that being a junior designer is not about having a portfolio...” But the fact is that we all would like to see some results of your work, even if it is your very early work on a few design projects or concepts. Remember, if you have something to show, this would always be a considerable advantage!
I have heard from some juniors that they don’t want to invest time in their portfolio because this work is not payable and it’s time-consuming. But sitting and waiting and getting rejected again and again is also time-consuming. And spending a few of your first career years in the wrong company is also time-consuming (and disappointing, too). So my advice is to spend some time in advance on showcasing your work and then get much better results in the near future.
In case you need some extra motivation, here is a quote from Muhammad Ali, regarded as one of the most significant sports figures of the 20th century:
“I hated every minute of training, but I said to myself, ‘Do not quit. Suffer now and live the rest of your life as a champion.’”
— Muhammad Ali
Ready to fire but have no idea where to start? Here are a few options:
- Find a popular product with a rather difficult-to-use or not very elegant interface and research what the users of this product are complaining about the most. Then, as an exercise, design a few interface screens for this product, with their core features explained, publish them on social media, and tag that company. (This approach may not always work, but it’s worth a try.)
- Sign up for and actively participate in hackathons. As a result, it’s possible that you may get not just a few screens redesigned in Figma but a real working product you can show (and be proud of). Also, you can meet nice people there who may recommend you if you apply for a job at one of the companies they work for.
- Complete UXchallenge challenges and present how you solved them on LinkedIn.
Note: You’re not limited to LinkedIn, of course; you can also use Instagram, Facebook, Behance, Dribbble, and so on. But keep in mind that many recruiters prefer LinkedIn. - Pick up a website that you use often and check whether it meets the “Ten Usability Heuristics for User Interface Design.” Create a detailed report that lists everything that can be (re)designed better. Publish the report on LinkedIn and also send it to the company that made this website. Don’t forget to tell them why you did that report for their website specifically and that you’re learning UX design, practicing, and actively looking for a job.
- Visit some popular developer conferences where you would be one of the only designers attending. Talk to people and propose your help for their startups. Who knows, you may become the co-creator of some future cool startup!
- Choose an area where digitalization hasn’t propagated yet and create a design concept using very modern technologies. For instance, people have been growing plants for thousands of years, but data analysis and visualization dramatically changed the efficiency of that process only lately. The agricultural industry has undergone a remarkable transformation thanks to UX design — a crucial element in ensuring that agricultural applications are not just functional but also intuitive and user-friendly. From precision farming to crop monitoring systems, digital tools have revolutionized the way farmers manage their operations.
Note: You can check the following article for details: “The Evolution of UX Design in Agricultural Applications.”
Don’t wait until someone hands you your chance on a “silver platter.” There are many projects that need the designer’s hands and help but can’t get such help yet. Assist them and then show the results of your work in your first portfolio. It gives you a huge advantage over other candidates who haven’t worked on their portfolios yet!
Preparing For Your First Interviews: Getting A First JobFrom what I’ve heard, getting the first job is the biggest problem for a junior designer, so I will focus on this part in more detail.
Applying For A Job
To reach the goal, you should formulate it correctly. It’s already formulated in this case, but most candidates understand it wrong. The right goal here is to be invited to an interview — not to get an offer right now or tell everything about your life in the CV document. You just need to break through the first level of filtering.
Note: Some of these tips are for absolute beginners. Do they sound too obvious to you? Apologies if so. However, all of them are based on my personal experience, so I think there are no tips that I should omit.
- Send your CV and motivational letter (if required in the job description) from the correct email address. It’s always strange to receive a job application from an email such as ‘sad.batman2006@gmail.com’. Seniors are always responsible for the tasks that junior designers complete, and we want to know that you are a seriously-minded and responsible person to help us do our work. Small details, such as the email address you would use to get in touch, do matter.
- Use your real name. I’ve had cases where people have used different names in their emails and CVs. I think it’s too obvious why this will look very strange, so I won’t spend time describing it in detail.
- Skill representations. Use the well-accepted standards. I have seen some CVs created with the help of services such as CV Maker where skills (level of English, how well you know Figma, Illustrator, and other design tools, and so on) were represented as loaders or diagrams. But there are existing standards, so use them in order to be understood better. For instance, if you describe your level of English knowledge, use the CEFR levels (A1/A2, B1/B2, C1/C2). Don’t make people interpret a diagram instead.
- Check/proofread the text in your email, CV, and portfolio. We expect that you may not know everything about design, but spelling errors don’t demonstrate exactly your desire to learn and your attention to detail. You can use Grammarly or ChatGPT to check your text, but you should not try to substitute your thoughts with some AI-“generated” ideas. Also, make sure to structure well the content of your CV and to format it properly.
- Read the job description carefully, find matches with your skills, and reflect these in the CV. Recruiters cannot review all the CVs thoroughly. Remember, the goal is to break through the first level of filtering — the recruiter is not a designer and can’t evaluate you and your skills. However, the recruiter can decide whether your CV is relevant to the job description, so it’s very important to tweak the CV by making sure you mention all the skills that you possess and that match the ones found in the specific job description.
- Don’t count solely on the job application form posted on the company’s website. There were cases when I had no reply after filling out and submitting the official application form but then got an offer after trying to reach a recruiter from that company directly on LinkedIn or via some other available communication channel. So don’t be shy to get in touch directly.
- Avoid using PDF documents for portfolios or anything else that people need to download before opening. The more time it takes to open and review your portfolio, the less time people will spend checking what’s in it. A link to your portfolio on the web will always work better, and it’s also a much more professional approach! You can use platforms such as Behance (or similar), or you can create your case studies in Figma and paste the shareable link into your CV.
Note: There are many ways to show your portfolio, and Figma is only one of them. For ideas, you can check “Figma Portfolio Templates & Examples” (a curated selection of portfolio templates for Figma). Or even better, you can self-host your portfolio on your own domain and website; however, this may require some more advanced technical skills and knowledge, so you can leave this idea for later.
Completing A Test Task
The test task aims to assess what we can expect from you in the workplace. And this is not just about the quality of your design skills — it’s also about how you will communicate with others and how you will be able to propose practical solutions to problems.
What do I mean by “practical solutions”? In the real world, designers always work within certain limitations (constraints), such as time, budget, team capacity, and so on. So, if you have some bright ideas that are likely very hard to implement, keep these for the interview. The test task is a way to show that you are someone who can define the correct problems and do the proper work, e.g. find the solutions to them.
A few words of advice on how to do exactly that:
- If you have a chance to speak to the target audience, do it, especially if the test task is to make an existing product better. You don’t have to do complete research, but if it’s a popular product that everyone uses, you can ask your friends about their experience of using it. If it’s not, check what people say on Reddit, in reviews on the Apple App Store, or on Google Play. Find video reviews of this product on YouTube and analyze the comments under the video. Also, take a look at similar products and what people say about them. Defining real problems is a key skill for designers.
Note: How can we we conduct UX research when there is no or only limited access to users? Vitaly Friedman outlines a few excellent strategies in his article on this topic: “Why Designers Aren’t Understood.” - Prioritize features that you see and can reflect on in the test task. You can use the Kano model or another framework, but don’t skip this step! It is sometimes puzzling to see candidates spending a lot of time on dark mode UI mockups but failing to work on the required key features instead.
Note: The Kano Analysis model is a tool that enables you to understand how customer emotional responses to products or features can be measured and explored. - If you need more time, say so. It also will show what your behavior will be when working on a real project. Speaking about the problem at the last moment can bring big troubles to the team. Also — happened in my practice in a few cases — it’s strange to hear:
- “I didn’t fully complete the test task because I was busy.”
- OK, if you are too busy (with other things?), then we will have to interview some other candidates.
My advice is to show dedication and focus toward your current job application assignment.
- In some cases, the candidates try to go the “extra mile” by doing more things than were initially asked of them, but with lower quality. Unfortunately, It doesn’t work this way. Instead, you need to do less but better. Of course, there could be exclusions in some cases, like when you do sketching and prototyping, where showing rough ideas is perfectly OK. So, try to find the balance between the volume and quality of your work. Showing many (but weak) mockups in order to impress with the volume of your work (instead of the quality) is not a good idea.
- Sometimes, we ask to redesign a screen as a test task. This is not about using better/shinier UI components. Instead, try to understand the user goals on that screen and then think about the most suitable UI components that you can use to serve these user goals.
Recommendations For The Interview
The interview is the most challenging part because the most optimal way to prepare for it depends on the specific company where you’re applying for the job and the interviewer’s experience. But there are still a few “universal” things you can do in order to increase your chances:
- If I was restricted to giving only one piece of advice, I would say: Be sincere! It’s not an exam, so don’t try to guess the answer if you don’t know it. No one knows everything, and it’s OK — be honest and it will pay off.
- Research the company and the role before the interview. Check the company’s portfolio, cases, products, and so on, and even look up the names and titles of designers working there.
Note: It will help a lot if the company has an About → The Team page on its website; but if not, using LinkedIn will probably help, too.) When you have researched the role in detail, it will help you define which of your skills will be a good match and you could then highlight them during the interview. - The core questions in a UX design interview are not a secret. Usually, it’s about the design phases, your experience, hobbies, motivation, and so on. Work on these questions and clarify the answers before going to the interview. Just write them down and read them out loudly. Try to check how it sounds. Converting your design experience into exact words requires brain energy, especially if somebody in front of you is waiting for the answer, so do it beforehand, and you’ll feel much better prepared — and calmer.
- Listen carefully to the questions you are being asked. Ask the interviewer to clarify if you do not understand a question completely. It’s always weird when the candidate gives an answer that is not related to the question you asked.
- Don’t be late. Do your best to be on time.
- If it’s an online interview, check the time zones, the communication tools, and everything else. There’s nothing worse than starting Zoom (or another app that you know you’ll need) at the last minute and discovering that it needs an urgent update. Precious minutes will be lost during the update process while the other party will be patiently waiting for you to come online. And you better also check your headphones, microphone, camera, and Bluetooth connection before the start of the meeting.
- Similarly, if it’s an in-person interview, plan your trip in advance and add some extra time for something unexpected; better if you arrive early than late. The problem is not only about wasting someone’s time; it’s about your emotional balance. If you are late, you will be nervous and make mistakes that you otherwise wouldn’t.
- Don’t look for a job in the companies of your dreams right from the start. First, pass a few interviews with other companies, get feedback, do some retrospectives, gain some real experience, and be prepared to show your best when you get your chance.
- Be yourself, but also clearly communicate who you are going to be as people with goals and a plan always make a better impression. Most companies don’t hire juniors — they hire future middle-level and senior designers. And if you feel a certain company where you’re applying for a job would not support you in this way, better try another one. The first few years are the foundation of your future career, so do your best to get into a company where you can grow as a designer.
Thank you for following me so far! Hopefully, you have learned your design tools, worked on your portfolio, and prepared meticulously for your first interviews. If all goes according to plan, sooner or later, you’ll get your first junior UX job. And then you’ll face more challenges, about which I will speak in detail in the second part of my two-part article series.
But before that, do check Further Reading, where I have gathered a few resources that will be very useful if you are just about to begin your UX design career.
Further Reading
Basic Design Resources
- “UX Crash Course: 31 Fundamentals,” Joel Marsh
- “UX Crash Course: 30 Stupid Questions,” Joel Marsh
- “UX Crash Course: User Psychology,” Joel Marsh
- “What’s The Perfect Design Process?,” Vitaly Friedman
- “10 Usability Heuristics for User Interface Design,” Jakob Nielsen
- “10 Advanced Tips For A Design Portfolio,” Slava Shestopalov
A List of Design Resources from the Nielsen Norman Group
- Context Methods, Kate Moran and Mayya Azarova
- Design Pattern Guidelines, Samhita Tankala and Alita Joyce
- Design Thinking, Kate Moran and Megan Brown
- DesignOps, Kate Kaplan
- Facilitation, Kate Kaplan
- Information Architecture, Page Laubheimer
- Intranet & Enterprise Design, Kara Pernice
- Lean & Agile, Anna Kaley
- Mobile UX, Raluca Budiu
- Omnichannel & Customer Experience, Kim Salazar
- Personas, Kate Kaplan
- Psychology for UX, Tanner Kohler
- ResearchOps, Kate Kaplan
- Remote Usability Testing, Kate Moran
- Service Design, Sarah Gibbons
- UX Basics, Tim Neusesser
- UX Careers, Taylor Dykes
- UX Mapping Methods, Kate Kaplan
- UX Stakeholders, Sarah Gibbons
- UX Writing, Anna Kaley
- Qualitative Usability Testing, Kate Moran
- Quantitative Research, Kate Moran
- Visual Design in UX, Kelley Gordon
The Era Of Platform Primitives Is Finally Here
This article is a sponsored by Netlify
In the past, the web ecosystem moved at a very slow pace. Developers would go years without a new language feature or working around a weird browser quirk. This pushed our technical leaders to come up with creative solutions to circumvent the platform’s shortcomings. We invented bundling, polyfills, and transformation steps to make things work everywhere with less of a hassle.
Slowly, we moved towards some sort of consensus on what we need as an ecosystem. We now have TypeScript and Vite as clear preferences—pushing the needle of what it means to build consistent experiences for the web. Application frameworks have built whole ecosystems on top of them: SolidStart, Nuxt, Remix, and Analog are examples of incredible tools built with such primitives. We can say that Vite and TypeScript are tooling primitives that empower the creation of others in diverse ecosystems.
With bundling and transformation needs somewhat defined, it was only natural that framework authors would move their gaze to the next layer they needed to abstract: the server.
Server PrimitivesThe UnJS folks have been consistently building agnostic tooling that can be reused in different ecosystems. Thanks to them, we now have frameworks and libraries such as H3 (a minimal Node.js server framework built with TypeScript), which enables Nitro (a whole server runtime powered by Vite, and H3), that in its own turn enabled Vinxi (an application bundler and server runtime that abstracts Nitro and Vite).
Nitro is used already by three major frameworks: Nuxt, Analog, and SolidStart. While Vinxi is also used by SolidStart. This means that any platform which supports one of these, will definitely be able to support the others with zero additional effort.
This is not about taking a bigger slice of the cake. But making the cake bigger for everyone.
Frameworks, platforms, developers, and users benefit from it. We bet on our ecosystem together instead of working in silos with our monolithic solutions. Empowering our developer-users to gain transferable skills and truly choose the best tool for the job with less vendor lock-in than ever before.
Serverless Rejoins ConversationSuch initiatives have probably been noticed by serverless platforms like Netlify. With Platform Primitives, frameworks can leverage agnostic solutions for common necessities such as Incremental Static Regeneration (ISR), Image Optimization, and key/value (kv) storage.
As the name implies, Netlify Platform Primitives are a group of abstractions and helpers made available at a platform level for either frameworks or developers to leverage when using their applications. This brings additional functionality simultaneously to every framework. This is a big and powerful shift because, up until now, each framework would have to create its own solutions and backport such strategies to compatibility layers within each platform.
Moreover, developers would have to wait for a feature to first land on a framework and subsequently for support to arrive in their platform of choice. Now, as long as they’re using Netlify, those primitives are available directly without any effort and time put in by the framework authors. This empowers every ecosystem in a single measure.
Serverless means server infrastructure developers don’t need to handle. It’s not a misnomer, but a format of Infrastructure As A Service.
As mentioned before, Netlify Platform Primitives are three different features:
- Image CDN
A content delivery network for images. It can handle format transformation and size optimization via URL query strings. - Caching
Basic primitives for their server runtime that help manage the caching directives for browser, server, and CDN runtimes smoothly. - Blobs
A key/value (KV) storage option is automatically available to your project through their SDK.
Let’s take a quick dive into each of these features and explore how they can increase our productivity with a serverless fullstack experience.
Image CDN
Every image in a /public can be served through a Netlify function. This means it’s possible to access it through a /.netlify/images path. So, without adding sharp or any image optimization package to your stack, deploying to Netlify allows us to serve our users with a better format without transforming assets at build-time. In a SolidStart, in a few lines of code, we could have an Image component that transforms other formats to .webp.
import { type JSX } from "solid-js";
const SITE_URL = "https://example.com";
interface Props extends JSX.ImgHTMLAttributes<HTMLImageElement> {
format?: "webp" | "jpeg" | "png" | "avif" | "preserve";
quality?: number | "preserve";
}
const getQuality = (quality: Props["quality"]) => {
if (quality === "preserve") return"";
return &q=${quality || "75"};
};
function getFormat(format: Props["format"]) {
switch (format) {
case "preserve":
return" ";
case "jpeg":
return &fm=jpeg;
case "png":
return &fm=png;
case "avif":
return &fm=avif;
case "webp":
default:
return &fm=webp;
}
}
export function Image(props: Props) {
return (
<img
{...props}
src={${SITE_URL}/.netlify/images?url=/${props.src}${getFormat(
props.format
)}${getQuality(props.quality)}}
/>
);
}
Notice the above component is even slightly more complex than bare essentials because we’re enforcing some default optimizations. Our getFormat method transforms images to .webp by default. It’s a broadly supported format that’s significantly smaller than the most common and without any loss in quality. Our get quality function reduces the image quality to 75% by default; as a rule of thumb, there isn’t any perceivable loss in quality for large images while still providing a significant size optimization.
Caching
By default, Netlify caching is quite extensive for your regular artifacts - unless there’s a new deployment or the cache is flushed manually, resources will last for 365 days. However, because server/edge functions are dynamic in nature, there’s no default caching to prevent serving stale content to end-users. This means that if you have one of these functions in production, chances are there’s some caching to be leveraged to reduce processing time (and expenses).
By adding a cache-control header, you already have done 80% of the work in optimizing your resources for best serving users. Some commonly used cache control directives:
{
"cache-control": "public, max-age=0, stale-while-revalidate=86400"
}public: Store in a shared cache.max-age=0: resource is immediately stale.stale-while-revalidate=86400: if the cache is stale for less than 1 day, return the cached value and revalidate it in the background.
{
"cache-control": "public, max-age=86400, must-revalidate"
}
public: Store in a shared cache.max-age=86400: resource is fresh for one day.must-revalidate: if a request arrives when the resource is already stale, the cache must be revalidated before a response is sent to the user.
Note: For more extensive information about possible compositions of Cache-Control directives, check the mdn entry on Cache-Control.
The cache is a type of key/value storage. So, once our responses are set with proper cache control, platforms have some heuristics to define what the key will be for our resource within the cache storage. The Web Platform has a second very powerful header that can dictate how our cache behaves.
The Vary response header is composed of a list of headers that will affect the validity of the resource (method and the endpoint URL are always considered; no need to add them). This header allows platforms to define other headers defined by location, language, and other patterns that will define for how long a response can be considered fresh.
The Vary response header is a foundational piece of a special header in Netlify Caching Primitive. The Netlify-Vary will take a set of instructions on which parts of the request a key should be based. It is possible to tune a response key not only by the header but also by the value of the header.
- query: vary by the value of some or all request query parameters.
- header: vary by the value of one or more request headers.
- language: vary by the languages from the
Accept-Languageheader. - country: vary by the country inferred from a GeoIP lookup on the request IP address.
- cookie: vary by the value of one or more request cookie keys.
This header offers strong fine-control over how your resources are cached. Allowing for some creative strategies to optimize how your app will perform for specific users.
Blob Storage
This is a highly-available key/value store, it’s ideal for frequent reads and infrequent writes. They’re automatically available and provisioned for any Netlify Project.
It’s possible to write on a blob from your runtime or push data for a deployment-specific store. For example, this is how an Action Function would register a number of likes in store with SolidStart.
import { getStore } from "@netlify/blobs";
import { action } from "@solidjs/router";
export const upVote = action(async (formData: FormData) => {
"use server";
const postId = formData.get("id");
const postVotes = formData.get("votes");
if (typeof postId !== "string" || typeof postVotes !== "string") return;
const store = getStore("posts");
const voteSum = Number(postVotes) + 1)
await store.set(postId, String(voteSum);
console.log("done");
return voteSum
});
- Check
@netlify/blobsAPI documentation for more examples and use-cases.
With high-quality primitives, we can enable library and framework creators to create thin integration layers and adapters. This way, instead of focusing on how any specific platform operates, it will be possible to focus on the actual user experience and practical use-cases for such features. Monoliths and deeply integrated tooling make sense to build platforms fast with strong vendor lock-in, but that’s not what the community needs. Betting on the web platform is a more sensible and future-friendly way.
Let me know in the comments what your take is about unbiased tooling versus opinionated setups!
10 Copywriting Tips to Boost WordPress Conversions
 If you want to start your business effortlessly, WordPress is the best platform, regardless of the business type. After building your website, you would naturally aim to drive traffic to your website. To succeed, you need to convert the site visitors into customers. And that’s where copywriting comes in. But the thing is, the copies […]
If you want to start your business effortlessly, WordPress is the best platform, regardless of the business type. After building your website, you would naturally aim to drive traffic to your website. To succeed, you need to convert the site visitors into customers. And that’s where copywriting comes in. But the thing is, the copies […]
The post 10 Copywriting Tips to Boost WordPress Conversions appeared first on WPExplorer.
How To Fix SQL Database Restore Failed, Database Is in Use?
When restoring the SQL Server database from backup, you may encounter the “Restore of database failed, Database is in use” error message. This happens if someone is running queries or if you have an active connection or active windows running on the database to be restored.
The complete error message looks like the following: