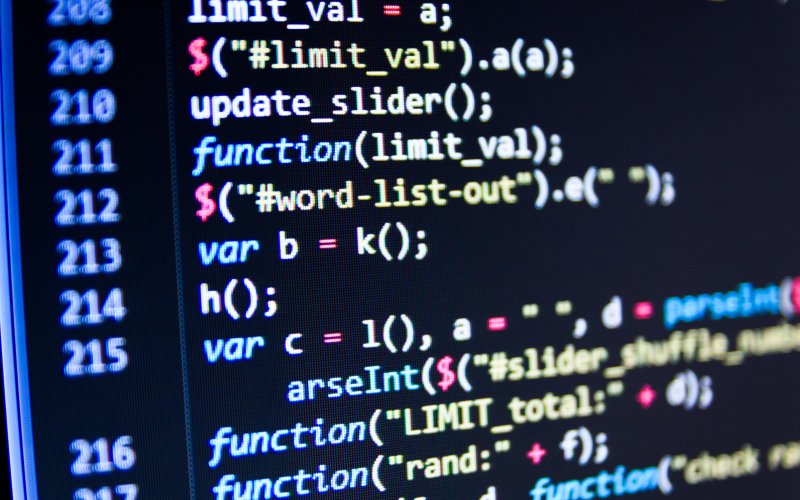
<?php
$pdo = new PDO('mysql:host=localhost;port=3306;dbname=crud', 'root', '');
$pdo->setAttribute(PDO::ATTR_ERRMODE, PDO::ERRMODE_EXCEPTION);
$title = $_POST=['title'];
$description = $_POST = ['description'];
$price = $_POST = ['price'];
$date = date('Y-m-d H:i:s');
$products = $statement = $pdo->prepare("INSERT INTO products (title, image, description, price, Create_date)
VALUES (:title, :image, :description, :price, :date)");
$statement->bindValue(':title', $title);
$statement->bindValue(':image', '');
$statement->bindValue(':description', $description);
$statement->bindValue(':price', $price);
$statement->bindValue(':date', $date);
$statement->execute();
?>Jenny B Kowalski’s A-Z (and a-z) as Variable Letterforms
Jenny B Kowalski has been posting a-letter-a-day on Instagram exploring multi-axis variable/responsive letterforms. They are very clever in that one of the axes controls an uppercase-to-lowercase conversion, literally morphing the shape of the letters from an uppercase version to a lowercase version. The other axis is a stroke weight, which also dramatically changes the feel of the letters.
Here’s Q, one of my favorites:
She’s using p5.js, but I don’t see any reason these couldn’t be made into a variable font with custom axes.
OK here’s one more. I find the I/i very clever:
The post Jenny B Kowalski’s A-Z (and a-z) as Variable Letterforms appeared first on CSS-Tricks.
You can support CSS-Tricks by being an MVP Supporter.
This Week In Web Design – April 30, 2021
How To Create A Dropdown Menu In WordPress
How do you submit a website to Google?
How do you submit a website to Google?